Lab 3.6.5 Sharing Resources
Langkah 1: Share folder
- Klik Mulai. dari Menu Start, pilih All Programs, Accessories, dan kemudian Windows Explorer.
- Pada panel Folder, klik tanda plus () di samping My Computer. Klik C: drive. Dari File yang
menu. pilih New dan dari sub-menu, pilih opsi Folder. Jenis Saham sebagai nama
folder. - Klik kanan Share folder baru dan pilih Properties. Catatan: Pilihan Berbagi tidak tersedia untuk Documents and Settings, Program Files, dan Windows sistem folder.
- Pilih tab Sharing. Pada kotak dialog Properties Share, klik Share this folder tombol radio
berbagi folder dengan pengguna lain pada jaringan Anda. Nama default untuk folder bersama adalah sama nama sebagai nama folder asli. CATATAN: Untuk mengubah nama folder pada jaringan, ketik nama baru untuk folder di Berbagi nama kotak teks. Ini tidak akan mengubah nama folder pada komputer Anda. - Klik Apply dan kemudian OK.
- Buat file teks menggunakan Notepad dan simpan ke folder Share. Pada desktop Windows XP, klik Start, pilih All Programs, Accessories, lalu Notepad. Dalam aplikasi Notepad, ketik pesan “Hello World!”. Dari menu File, pilih Simpan. Pada kolom File name, ketik “pesan Test”. Klik ikon dengan folder dan panah atas seperti ditunjukkan pada gambar berikut.
- Klik dua kali Komputer Saya, kemudian klik dua kali drive C:. Cari dan klik dua kali folder Share, kemudian klik Simpan.
- Tutup aplikasi Notepad.
- Ulangi langkah 1 – 5 untuk mesin Windows XP Professional kedua dengan pengecualian berikut:
Langkah 2: Peta drive jaringan untuk menyediakan akses cepat dan mudah ke folder shared
- Pada workstation XP pertama Windows, klik Start, pilih All Programs, Accessories, dan kemudian Windows Explorer.
- Pada panel Folder, klik My Computer. Dari Tools Menu, pilih Map Network Drive ….
- Dalam textbox Drive, pilih huruf drive yang tidak terpakai menggunakan menu pulldown.
- Pertanyaan: Apa huruf drive yang Anda pilih
- Di bidang Folder, ketik alamat IP PC remote dan nama bagian remote menggunakan format: \ \ ip_address \ sharename
- Klik Finish. Sebuah jendela akan muncul dengan pesan Mencoba untuk terhubung ke \ \ 192.168.10.3 \ share2. Sebuah jendela akan terbuka untuk menampilkan isi dari folder bersama Share2 disebut yang sekarang sudah diberi huruf drive. CATATAN: Alamat IP dapat digantikan dengan nama komputer.\
- Klik dua kali pesan Test 2 dokumen teks. Tambahkan aturan kata-kata teknisi untuk dokumen. Dari menu File dan pilih Simpan. Pertanyaan: Apa pesan yang ditampilkan? Mengapa Anda pikir ini terjadi? Jawaban: Tidak dapat mengakses file ini. Periksa Keistimewaan Keamanan. Pertanyaan kedua adalah pendapat pelajar sendiri
- File-file dalam folder bersama secara otomatis dilindungi dalam versi Windows XP Professional. Klik OK di kotak pesan. Klik Batalkan, kemudian klik Tutup untuk pesan Uji 2 dokumen.
- Pada kotak pesan, klik No untuk menutup dokumen tanpa menyimpan perubahan.
- Ulangi prosedur ae bawah Langkah 2 untuk memetakan drive pada workstation Windows XP kedua. Ini drive harus dipetakan ke bagian Anda dikonfigurasi pada Langkah 1.
- Dari mesin XP pertama Windows Professional, klik Start, pilih All Programs, kemudian Aksesoris, dan Windows Explorer.
- Expand My Computer dengan mengklik tanda plus () di samping pilihan.
- Daftar Windows Explorer akan menampilkan sebuah drive dengan label huruf drive yang Anda pilih untuk remote saham.
- Ulangi ac untuk mesin Windows XP Professional kedua prosedur. Jika huruf drive muncul pada kedua komputer, maka folder dibagi dan drive yang dipetakan benar pada kedua Windows XP workstation. Anda dapat melakukan langkah yang sama di folder apapun. Ketika
drive dengan benar dipetakan ke folder bersama, semua file dan folder di dalam folder bersama akan diakses dari workstation.
- Apa saja manfaat dipetakan drive dan folder berbagi di rumah atau kantor kecil
jaringan? Jawaban: menghidari terinfeksi dari virus dan memudahkan mengingat alamat file kita. - Folder yang tidak dapat dibagi? Dapatkah Anda memikirkan alasan mengapa sebuah sistem operasi mungkin tidak mengizinkan jenis tertentu folder yang akan dibagi? Jawaban: mungkin ada konfigurasi yang salah.
- Sebuah drive yang dipetakan menyediakan pointer ke sumber daya jaringan, tapi huruf drive yang dipetakan dikatakan signifikan secara lokal saja. Menurut Anda apa yang dimaksud dengan lokal yang signifikan?
Lab 6.2.5 Configuring BGP with Default Routing
| Equipment / media | price | quality |
| USB and solid-state drives | $30-$90 | medium |
| fireWire drives | $180 | best |
| CD-RW and DVD+RW/-RW drives | $100 | medium |
CCNA2 – Lab 5.1.2 Powering Up an Integrated Services Router
- Set up a new Cisco 1841 Integrated Services Router ( ISR ).
- Connect a computer to the router console interface.
- Configure Hyper Terminal so that the computer can communicate with the router
- Cisco 1841 ISR other comparable router.
- Power Cable
- Windows PC with terminal emulation program
- RJ45-to-DB9 connector console cable.
1
Refer to the exhibit. What two statements can be concluded from the information that is shown in the exhibit? (Choose two.)
All ports that are listed in the exhibit are access ports.
ARP requests from Host1 will be forwarded to Host2.
Attaching Host1 to port 3 will automatically allow communication between both hosts.
The default gateway for each host must be changed to 192.168.3.250/28 to allow communication between both hosts.
A router connected to the switch is needed to forward traffic between the hosts.
2
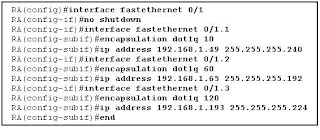
A router is configured to connect to a trunked uplink as shown in the exhibit. A packet is received on the FastEthernet 0/1 physical interface from VLAN 10. The packet destination address is 192.168.1.120. What will the router do with this packet?
The router will forward the packet out interface FastEthernet 0/1.1 tagged for VLAN 10.
The router will forward the packet out interface FastEthernet 0/1.2 tagged for VLAN 60.
The router will forward the packet out interface FastEthernet 0/1.3 tagged for VLAN 60.
The router will forward the packet out interface FastEthernet 0/1.3 tagged for VLAN 120.
The router will not process the packet since the source and destination are on the same subnet.
The router will drop the packet since no network that includes the source address is attached to the router.
3 The information contained in a BPDU is used for which two purposes? (Choose two.)
to prevent loops by sharing bridging tables between connected switches
to set the duplex mode of a redundant link
to determine the shortest path to the root bridge
to determine which ports will forward frames as part of the spanning tree
to activate looped paths throughout the network
4 A router has two serial interfaces and two Fast Ethernet interfaces. This router must be connected to a WAN link and to a switch that supports four VLANs. How can this be accomplished in the most efficient and cost-effective manner to support inter-VLAN routing between the four VLANs?
Connect a smaller router to the serial interface to handle the inter-VLAN traffic.
Add two additional Fast Ethernet interfaces to the router to allow one VLAN per interface.
Connect a trunked uplink from the switch to one Fast Ethernet interface on the router and create logical subinterfaces for each VLAN.
Use serial-to-Fast Ethernet transceivers to connect two of the VLANs to the serial ports on the router. Support the other two VLANs directly to the available FastEthernet ports.
5 When are MAC addresses removed from the CAM table?
at regular 30 second intervals
when a broadcast packet is received
when the IP Address of a host is changed
after they have been idle for a certain period of time
6
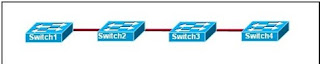
Refer to the exhibit. Switch1 is not participating in the VTP management process with the other switches. Which two are possible reasons for this? (Choose two.)
Switch2 is in transparent mode.
Switch1 is in client mode.
Switch1 is using VTP version 1 and Switch2 is using VTP version 2.
Switch2 is in server mode.
Switch1 is in a different management domain.
Switch1 has no VLANs.
7 Which three must be used when a router interface is configured for VLAN trunking? (Choose three.)
one subinterface per VLAN
one physical interface for each subinterface
one IP network or subnetwork for each subinterface
one trunked link per VLAN
a management domain for each subinterface
a compatible trunking protocol encapsulation for each subinterface
8
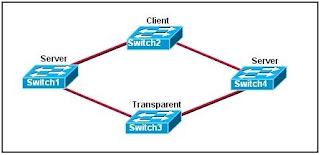
Refer to the exhibit. The switches are connected with trunks within the same VTP management domain. Each switch is labeled with its VTP mode. A new VLAN is added to Switch3. This VLAN does not show up on the other switches. What is the reason for this?
VLANs cannot be created on transparent mode switches.
Server mode switches neither listen to nor forward VTP messages from transparent mode switches.
VLANs created on transparent mode switches are not included in VTP advertisements.
There are no ports assigned to the new VLAN on the other switches.
Transparent mode switches do not forward VTP advertisements.
9 Which two criteria are used by STP to select a root bridge? (Choose two.)
memory size
bridge priority
switching speed
number of ports
base MAC address
switch location
10 Which three steps should be taken before moving a Catalyst switch to a new VTP management domain? (Choose three.)
Reboot the switch.
Reset the VTP counters to allow the switch to synchronize with the other switches in the domain.
Download the VTP database from the VTP server in the new domain.
Configure the VTP server in the domain to recognize the BID of the new switch.
Select the correct VTP mode and version.
Configure the switch with the name of the new management domain.
11 Which two items will prevent broadcasts from being sent throughout the network? (Choose two.)
bridges
routers
switches
VLANs
hubs
12 Which two characteristics describe a port in the STP blocking state? (Choose two.)
provides port security
displays a steady green light
learns MAC addresses as BPDUs are processed
discards data frames received from the attached segment
receives BPDUs and directs them to the system module
13 What is the first step in the process of convergence in a spanning tree topology?
election of the root bridge
determination of the designated port for each segment
blocking of the non-designated ports
selection of the designated trunk port
activation of the root port for each segment
14 In which STP state does a switch port transmit user data and learn MAC addresses?
blocking
learning
disabling
listening
forwarding
15 What is the purpose of VTP?
maintaining consistency in VLAN configuration across the network
routing frames from one VLAN to another
routing the frames along the best path between switches
tagging user data frames with VLAN membership information
distributing BPDUs to maintain loop-free switched paths
16 Which statement best describes adaptive cut-through switching?
The switch initially forwards all traffic using cut-through switching and then changes to store-and-forward switching if errors exceed a threshold value.
The switch initially forwards all traffic using cut-through switching and then changes to fast-forward switching if errors exceed a threshold value.
The switch initially forwards all traffic using cut-through switching and then temporarily disables the port if errors exceed a threshold value.
The switch initially forwards all traffic using store-and-forward switching and then changes to cut-through switching if errors exceed a threshold value.
17 Using STP, how long does it take for a switch port to go from the blocking state to the forwarding state?
2 seconds
15 seconds
20 seconds
50 seconds
18
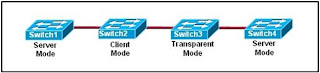
Refer to the exhibit. The switches are interconnected by trunked links and are configured for VTP as shown. A new VLAN is added to Switch1. Which three actions will occur? (Choose three.)
Switch1 will not add the VLAN to its database and will pass the update to Switch 2.
Switch2 will add the VLAN to its database and pass the update to Switch3.
Switch3 will pass the VTP update to Switch4.
Switch3 will add the VLAN to its database.
Switch4 will add the VLAN to its database.
Switch4 will not receive the update.
Q.19 Which Catalyst feature causes a switch port to enter the spanning-tree forwarding state immediately?
backbonefast
uplinkfast
portfast
rapid spanning tree
20
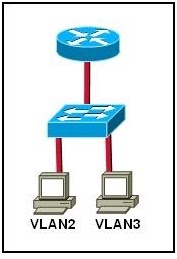
Refer to the exhibit. Which set of commands would be used on the router to provide communication between the two hosts connected to the switch?
Router(config)# interface vlan 2
Router(config-if)# ip address 192.168.2.1 255.255.255.0
Router(config-if)# no shutdown
Router(config)# interface vlan 3
Router(config-if)# ip address 192.168.3.1 255.255.255.0
Router(config-if)# no shutdown
Router(config)# interface fastethernet 0/0
Router(config-if)# no shutdown
Router(config-if)# interface fastethernet 0/0.2
Router(config-subif)# encapsulation dot1q 2
Router(config-subif)# ip address 192.168.2.1 255.255.255.0
Router(config-if)# interface fastethernet 0/0.3
Router(config-subif)# encapsulation dot1q 3
Router(config-subif)# ip address 192.168.3.1 255.255.255.0
Router(config)# interface vlan 2
Router(config-if)# switchport mode trunk dot1q
Router(config)# interface vlan 3
Router(config-if)# switchport mode trunk dot1q
Router(config)# interface fastethernet 0/0
Router(config-if)# mode trunk dot1q 2 3
Router(config-if)# ip address 192.168.2.1 255.255.255.0
1 What type of connection point is a point of presence (POP)?
between a client and a host
between two local networks
between a computer and a switch
between an ISP and an Enterprise network
2 A network administrator needs to configure Telnet access to a router. Which group of commandsenable Telnet access to the router?
Router(config)# enable password class
Router(config)# line con 0
Router(config-line)# login
Router(config-line)# password cisco
Router(config)# ip host 192.168.1.1 NewYork
Router(config)# enable password cisco
Router(config)# line aux 0
Router(config-line)# login
Router(config-line)# password cisco
Router(config)# enable password class
Router(config)# line vty 0 4
Router(config-line)# login
Router(config-line)# password cisco
3 Which two types of information should be included in a business continuity plan? (Choose two.)
maintenance time periods
intrusion monitoring records
offsite data storage procedures
alternate IT processing locations
problem resolution escalation steps
4 Which two router parameters can be set from interface configuration mode? (Choose two.)
IP address
Telnet password
hostname
console password
subnet mask
enable secret password
5 Which two devices protect a corporate network against malicious attacks at the enterprise edge ?(Choose two.)
demarc
IP security (IPSec)
Data Service Unit (DSU)
intrusion prevention system (IPS)
intrusion detection system (IDS)
6 Which three steps must be performed to remove all VLAN information from a switch but retain therest of the configuration? (Choose three.)
Remove all VLAN associations from the interfaces.
Remove the 802.1q encapsulation from the interface
Issue the command copy start run.
Issue the command delete flash:vlan.dat.
Issue the command erase start.
Reload the switch.
7 What is the demarcation?
physical point where the ISP responsibilty ends and the customer responsibilty begins
physical location where all server farm connections meet before being distributed into the Core
point of entry for outside attacks and is often vulnerable
point of entry for all Access Layer connections from the Distribution Layer devices
8 Which device is responsible for moving packets between multiple network segments?
router
switch
CSU/DSU
IDS device
10 What information can an administrator learn using the show version command?
Cisco IOS filename
configured routing protocol
status of each interface
IP addresses of all interfaces
11 Which two situations require a network administrator to use out-of-band management to change arouter configuration? (Choose two.)
Network links to the router are down.
No Telnet password has been configured on the router.
The administrator can only connect to the router using SSH.
The network interfaces of the router are not configured with IP addresses.
Company security policy requires that only HTTPS be used to connect to routers.
12 It is crucial that network administrators be able to examine and configure network devices fromtheir homes. Which two approaches allow this connectivity without increasing vulnerability to externalattacks? (Choose two.)
Configure a special link at the POP to allow external entry from the home computer.
Set up VPN access between the home computer and the network.
Install a cable modem in the home to link to the network.
Configure ACLs on the edge routers that allow only authorized users to access management portson network devices.
Configure a server in the DMZ with a special username and password to allow external access.
13 A network administrator must define specific business processes to implement if a catastrophicdisaster prevents a company from performing daily business routines. Which portion of the networkdocumentation is the administrator defining?
business security plan
business continuity plan
network solvency plan
service level agreement
network maintenance plan
14 A DoS attack crippled the daily operations of a large company for 8 hours. Which two optionscould be implemented by the network administrator to possibly prevent such an attack in the future?(Choose two.)
install security devices with IDS and IPS at the enterprise edge
reset all user passwords every 30 days
filter packets based on IP address, traffic pattern, and protocol
deny external workers VPN access to internal resources
ensure critical devices are physically secure and placed behind the demarc
15 A network manager wants to have processes in place to ensure that network upgrades do not affectbusiness operations. What will the network manager create for this purpose?
business security plan
business continuity plan
service level agreement
network maintenance plan
16 An investment company has multiple servers that hold mission critical datThey are worried that ifsomething happens to these servers, they will lose this valuable information. Which type of plan isneeded for this company to help minimize loss in the event of a server crash?
business security
business continuity
network maintenance
service level agreement
17 When searching for information about authentication methods and usernames of companypersonnel, where can a network administrator look?
Business Continuity Plan
Business Security Plan
Network Maintenance Plan
Service Level Agreement
18 Refer to the exhibit. Which statement is true about port Fa5/1?
When a violation is detected, the port will log the information to a syslog server.
When a violation is detected, the port will go into err-disable mod
There have been 11 security violations since the last reload
The port is currently in the shutdown state.
1 What can be found at the enterprise edge?
Internet, VPN, and WAN modules
Internet, PSTN, and WAN services
server farms and network management
campus infrastructure, including access layer devices
2 In which functional area of the Cisco Enterprise Architecture should IDS and IPS be located to detect and prevent services from accessing hosts?
Enterprise Campus
Edge Distribution
Enterprise Edge
Service Provider Edge
3 A business consultant must use Internet websites to research a report on the e-business strategies of several firms and then electronically deliver the report to a group of clients in cities throughout the world. Which two teleworker tools can the consultant use to accomplish this project? (Choose two.)
VoIP
VPN
HTTP
Telnet
email
4 Which two measures help ensure that a hardware problem does not cause an outage in an enterprise LAN that supports mission critical services? (Choose two.)
providing failover capability
installing redundant power supplies
purchasing more bandwidth from the ISP
implementing broadcast containment with VLANs
installing routers that can handle a greater amount of throughput
5 Which task would typically only require services located at the access layer of the hierarchical design model?
connecting to the corporate web server to update sales figures
using a VPN from home to send data to the main office servers
printing a meeting agenda on a local departmental network printer
placing a VoIP call to a business associate in another country
responding to an e-mail from a co-worker in another department
6 How does a VPN work to support remote user productivity?
It uses SSL to encrypt remote user logins to the corporate intranet.
It uses secure Telnet for remote user connections to internal network devices.
It creates a virtual circuit that allows real-time communications between any two Internet endpoints.
It uses encapsulation to create a secure tunnel for transmission of data across non-secure networks.
7 A remote user needs to access a networking device on the internal network of the company. The transactions between the remote user and the device must be secure. Which protocol enables this to happen securely?
HTTP
SSH
Telnet
FTP
8 What does VoIP provide to telecommuters?
high-quality, live-video presentations
real-time voice communications over the Internet
ability to share desktop applications simultaneously
secure, encrypted data transmissions through the Internet
9 Which functional component of the Cisco Enterprise Architecture is responsible for hosting internal servers?
enterprise campus
enterprise edge
service provider edge
building distribution
10 What is the purpose of the Cisco Enterprise Architecture?
remove the three-layer hierarchical model and use a flat network approach
divide the network into functional components while still maintaining the concept of Core, Distribution, and Access Layers
provide services and functionality to the core layer by grouping various components into a single
component located in the access layer
reduce overall network traffic by grouping server farms, the management server, corporate intranet, and e-commerce routers in the same layer
11 Which two solutions would an enterprise IT department use to facilitate secure intranet access for remote workers? (Choose two.)
VPN
NAT
user authentication
client firewall software
packet sniffing
12 Which statement describes the difference between an enterprise WAN and an enterprise extranet?
An enterprise WAN is designed to interconnect local LANs, while an enterprise extranet is designed to interconnect remote branch offices.
An enterprise WAN is designed to interconnect branch offices, while an enterprise extranet is designed to give access to external business partners.
An enterprise WAN is designed to provide remote access for its teleworkers, while an enterprise extranet is designed to provide Internet connectivity for the enterprise.
An enterprise WAN is designed to provide Internet connectivity for the enterprise, while an enterprise extranet is designed to provide remote access to the enterprise network for teleworkers.
13 Why would a network administrator want to limit the size of failure domains when designing a network?
reduces the effect of Ethernet collisions
reduces the impact of a key device or service failure
reduces the impact of Internet congestion on critical traffic
reduces the impact of blocking broadcast packets at the edge of the local network
14 What is the main purpose of the Access Layer in a hierarchically designed network?
performs routing and packet manipulation
supplies redundancy and failover protection
provides a high-speed, low-latency backbone
serves as a network connection point for end-user devices
15 Which three functions are performed at the Distribution Layer of the hierarchical network model? (Choose three.)
forwards traffic that is destined for other networks
isolates network problems to prevent them from affecting the Core Layer
allows end users to access the local network
provides a connection point for separate local networks
transports large amounts of data between different geographic sites
forwards traffic to other hosts on the same logical network
16 What is a benefit of having an extranet?
It provides web-like access to company information for employees only.
It limits access to corporate information to secure VPN or remote access connections only.
It allows customers and partners to access company information by connecting to a public web server.
It allows suppliers and contractors to access confidential internal information using controlled external connections.
17 What are two important characteristics or functions of devices at the Enterprise Edge? (Choose two.)
providing Internet, telephone, and WAN services to the enterprise network
providing a connection point for end-user devices to the enterprise network
providing high-speed backbone connectivity with redundant connections
providing intrusion detection and intrusion prevention to protect the network against malicious activity
providing packet inspection to determine if incoming packets should be allowed on the enterprise network
18 Why is TCP the preferred Layer 4 protocol for transmitting data files?
TCP is more reliable than UDP because it requires lost packets to be retransmitted.
TCP requires less processing by the source and destination hosts than UDP.
UDP introduces delays that degrade the quality of the data applications.
TCP ensures fast delivery because it does not require sequencing or acknowlegements.
19 The ABC Corporation implements the network for its new headquarters using the Cisco Enterprise Architecture. The network administrator wants to filter the traffic from and to the outside world. Where should the administrator deploy a firewall device?
server farm
enterprise edge
enterprise campus
service provider edge
20 Which two statements are reasons why UDP is used for voice and video traffic instead of TCP?(Choose two.)
TCP requires all data packets to be delivered for the data to be usable.
The acknowledgment process of TCP introduces delays that break the streams of data.
UDP does not have mechanisms for retransmitting lost packets.
UDP tolerates delays and compensates for them.
TCP is a connectionless protocol that provides end-to-end reliability.
UDP is a connection-oriented protocol that provides end-to-end reliability
- Pada router Linksys, cari Ethernet (Local Area Network) LAN port. Ethernet LAN port terhubung jaringan host dan perangkat. Keempat LAN port dikelompokkan bersama di tengah router seperti yang ditunjukkan pada gambar berikut. CCNA Discovery Jaringan untuk Rumah dan Bisnis Kecil
- Pada PC, cari port Ethernet. Port dapat diintegrasikan ke dalam motherboard atau bisa juga
adaptor. Dalam kedua kasus, pelabuhan akan menjadi RJ-45 port. Foto menunjukkan port Ethernet pada adaptor.
- Hubungkan salah satu ujung yang lurus-melalui kabel Ethernet ke port Ethernet LAN pada router.
- Hubungkan ujung kabel yang lain ke port Ethernet PC.
- Ulangi prosedur ini untuk PC kedua.
- Untuk menetapkan alamat IP dan default gateway ke host Windows XP, dari menu Start, pilih Control Panel.
- Ada dua cara untuk melihat Control Panel: tampilan Klasik dan tampilan Kategori. Pilihan yang tersedia bergantung pada salah satu dari dua pandangan yang Anda gunakan. Jika Anda melihat opsi di kiri, mengatakan Beralih ke Kategori View, Anda sedang dalam modus tampilan Classic. Jika Anda melihat opsi di kiri yang mengatakan Beralih ke Classic View, Anda sedang dalam modus tampilan Kategori. Pastikan bahwa Anda berada di Modus tampilan klasik.
- Cari dan double-klik ikon Network Connections panel kontrol.
- Klik kanan ikon Local Area Connection yang mewakili NIC Anda dan klik menu Properties
pilihan. - Di jendela tengah, gulir ke bawah sampai Anda melihat dan bisa klik dua kali Internet Protocol (TCP / IP) pilihan. Gambar berikut menunjukkan bahwa opsi ini.
- Klik tombol Properties dan Internet Protocol [TCP / IP] Properties window akan muncul .. Selanjutnya, klik tombol Gunakan alamat IP berikut, yang mengaktifkan alamat IP, Subnet mask, dan Default gateway boks teks. Di bidang alamat IP, masukkan 192.168.10.2. Konfigurasi subnet mask ke 255.255.255.0. Konfigurasi gateway default ke 192.168.10.1. Gambar berikut menunjukkan bahwa pengaturan ini. (DNS server informasi tidak diperlukan pada saat ini, karenanya bidang di bawah Gunakan server DNS berikut Alamat tidak perlu diisi) Setelah selesai, klik OK..
- Dari Internet Protocol [TCP / IP] Properties window, klik OK untuk menerapkan perubahan. Bersabar, sejak langkah ini mungkin memakan waktu. Setelah perubahan diterapkan, Anda akan kembali ke Network Connections window.
- Karena dua komputer berada di jaringan yang sama, alamat IP mereka akan sama, subnet mereka masker akan sama, dan gateway default mereka akan identik. Lakukan prosedur yang sama pada PC kedua untuk menetapkan alamat IP, subnet mask, dan gateway default menggunakan berikut informasi:
- Mengapa Anda pikir alamat IP yang berbeda, tapi masker subnet dan gateway default adalah
sama? Jawaban: Setiap perangkat pada jaringan harus memiliki identifikasi unik. IP
alamat adalah salah satu cara unik mengidentifikasi setiap host jaringan atau perangkat. Default gateway merupakan cara berkomunikasi dengan perangkat yang TIDAK pada jaringan Anda sendiri
- Pada desktop Windows XP, klik Start.
- Dari menu Start, Pilih opsi menu Run.
- Dalam Buka: textbox, ketik cmd dan tekan Enter. Sebuah command prompt muncul. Angka-angka yang mengikuti menunjukkan proses ini.
- Pada baris command prompt, ketik ipconfig / all. Pastikan alamat IP dan gateway default
adalah nilai-nilai yang Anda masukkan pada langkah-langkah sebelumnya. Jika mereka salah, ulangi Langkah 3 dan 4. - Apakah alamat IP, subnet mask, dan gateway default yang benar untuk PC pertama? Jawaban: Ya
- Melakukan cek konfigurasi yang sama pada PC kedua. Jika nilai tidak benar, ulangi Langkah 3
dan 4. - Apakah alamat IP, subnet mask, dan gateway default benar untuk PC kedua? Jawaban: Ya
- CATATAN: Untuk menguji TCP / IP konektivitas antara PC, Windows Firewall harus dinonaktifkan sementara pada kedua PC. Windows Firewall harus diaktifkan kembali setelah tes telah selesai. Pada PC1, pada desktop Windows XP, klik Start. Dari menu Start, pilih Control Panel, dan klik dua kali Network Connections.
- Klik kanan ikon Local Area Connection dan pilih Properties. Klik tab Advanced. Cari dan
klik tombol Settings. - Buatlah catatan apakah pengaturan firewall yang ENABLED (ON) untuk port Ethernet atau CACAT (OFF) untuk port Ethernet.
- Jika pengaturan firewall diaktifkan, klik Nonaktif (tidak disarankan) tombol radio untuk menonaktifkan firewall. Pengaturan ini akan diaktifkan kembali dalam langkah selanjutnya. Klik OK di kotak dialog ini dan berikut untuk menerapkan pengaturan ini.
- Dari prompt perintah yang sama pada PC pertama, ketik ping 192.168.10.3 untuk menguji konektivitas dengan kedua PC.
- Jika ping berhasil, Anda akan melihat hasil yang mirip dengan gambar berikut. Jika ping tidak
sukses, lakukan langkah-langkah pemecahan masalah yang sesuai seperti memeriksa kabel dan memeriksa Anda alamat IP, subnet mask, dan tugas default gateway. - Dari command prompt pada PC kedua, ketik ping 192.168.10.2 untuk memeriksa konektivitas ke pertama PC. ping harus berhasil.
- Klik kanan Start dan pilih pilihan Explore.
- Berapa banyak huruf drive yang ditampilkan pada jendela yang muncul? Jawabannya tergantung pada perangkat keras yang diinstal, namun akan ada minimal satu dan paling mungkin dua
(Harddisk dan CD / DVD drive) - Yang huruf drive yang ditampilkan? Jawabannya tergantung pada perangkat keras yang terpasang, tetapi biasanya ada minimal C: drive untuk hard dan drive D: drive untuk drive CD / DVD
- Klik kanan ikon My Computer pada desktop Anda Windows XP dan pilih opsi Properties.
Jendela System Properties akan muncul. CATATAN: Jika ikon My Computer tidak muncul pada desktop, klik Start lalu klik kanan My Komputer. - Klik tab Nama Komputer. Sebuah contoh dari jendela yang muncul berikut:
- Klik Ubah. Membuat catatan dari nama komputer saat ini.
- Dalam Nama Komputer textbox, ketik PC1. Pastikan Anggota tombol radio atau bidang diatur ke
Workgroup. - Catat nama Workgroup.
- Klik OK. Jika diminta untuk restart komputer, klik OK untuk restart dan ikuti petunjuk pada layar.
- Gunakan proses yang sama untuk nama komputer PC2 kedua. Juga memastikan bahwa nama Workgroup adalah diatur ke nilai yang sama dengan PC1.
- Untuk memverifikasi konfigurasi baru, buka command prompt pada setiap komputer. Jika Anda lupa bagaimana, lihat untuk Langkah 4a, b, dan c.
- Gunakan perintah nbtstat untuk melihat dan mengumpulkan informasi tentang komputer remote. Dari command prompt, nbtstat jenis dan tekan Enter. Bantuan untuk menampilkan perintah seperti berikut: Huruf yang ditampilkan adalah pilihan disebut switch yang dapat anda gunakan dengan perintah nbtstat.
- Dari PC2, ketik perintah yang tepat untuk melihat informasi nbtstat PC1′s.
- The nbtstat-A (perhatikan bahwa saklar adalah modal A saat ini) dapat digunakan untuk melihat sama informasi dengan menggunakan alamat IP bukan nama. Jika Anda mengetik nbtstat lagi, Anda dapat melihat bahwa sintaks perintah memberitahu kita bahwa kita menggunakan-A diikuti dengan alamat IP. Alamat IP adalah bahwa dari remote komputer. Dari PC1, ketik nbtstat-A 192.168.10.3 untuk melihat informasi yang sama yang dikembalikan oleh nbtstat-perintah PC2.
- Tuliskan perintah yang akan diketik di PC2 untuk melihat informasi tentang PC1, menggunakan alamat IP dari PC1 bukan nama NetBIOS. nbtstat-A 192.168.10.3
- Dari PC1, anda dapat menggunakan perintah ping untuk memverifikasi konektivitas. Namun, daripada menggunakan IP alamat, Anda dapat menggunakan nama NetBIOS. Dari perintah PC1 PC2 prompt, ketik ping (pemberitahuan kapitalisasi). Hasilnya harus sukses.
- Dari PC1, ketik ping PC2 (kapitalisasi pemberitahuan).
- Apakah ping sukses menggunakan huruf kecil? ___________________________________ Ya
- Anda dapat menggunakan perintah nbtstat-r untuk melihat nama NetBIOS yang telah diselesaikan (mereka diketahui). Dari perintah PC1 dan PC2 prompt, nbtstat r-tipe untuk melihat bahwa komputer remote dikenal menggunakan NetBIOS.
- Tutup jendela command prompt.
- Jika jawaban untuk Langkah 5c adalah MATI atau ENABLED pada PC1, klik Start, pilih Control Panel, dan terbuka Jaringan Sambungan panel kontrol.
- Klik kanan ikon koneksi jaringan Ethernet dan pilih Properties. Klik tab Advanced. Cari dan klik Pengaturan.
- Jika pengaturan firewall yang cacat (dan mereka diaktifkan sebelum lab ini mulai), klik Di radio
tombol untuk menonaktifkan firewall. Klik OK di kotak dialog ini dan yang berikut ini untuk menerapkan pengaturan ini.
- Kembali ke Langkah 3 untuk mengubah alamat IP kembali ke yang asli.
- Kembali ke Langkah 6d untuk mengubah nama NetBIOS kembali ke yang asli.
- Pada meter kabel, pilih fungsi WIRE MAP dari tester kabel.
- Mengubah opsi setup dari tester kabel sampai tester diatur ke pengaturan kabel berikut.
- Untuk setiap kabel yang akan diuji menggunakan prosedur berikut. Tempat salah satu ujung kabel ke konektor RJ-45 jack berlabel UTP / FTP di tester. Pasang ujung kabel ke coupler RJ-45 perempuan, dan kemudian masukkan kabel pengenal ke sisi lain dari coupler. Para coupler dan kabel identifier adalah aksesoris yang datang dengan meter kabel banyak.
- The Wire Peta fungsi dan Kabel ID Unit dapat digunakan untuk menentukan kabel baik dari dekat dan jauh ujung kabel. Satu set angka yang ditampilkan pada layar LCD adalah akhir dekat, dan yang lainnya set ujung. Lakukan tes Kawat Peta pada setiap kabel yang disediakan. Isi dalam tabel berikut
- Menggunakan fungsi LENGTH tester, melakukan dasar
- Menggunakan jack kabel data dan patch panel dari laboratorium sebelumnya, hubungkan salah satu ujung dari salah satu lurus-melalui kabel Ethernet patch ke outlet jack data dan satu ujung straightthrough lain kabel ke jack di panel patch.
- Masukkan ujung salah satu kabel ke meter kabel dan ujung lainnya ke coupler dan
kabel identifier. Periksa kawat, panjang peta dan salah-kawat dari ujung ke ujung melalui kabel patch, jack data, dan patch panel. Apakah tes kabel dijalankan baik dari ujung ke ujung? Apa saja hasilnya? Jawaban: Wire peta: Straight-through.
- Jika Anda berada di pekerjaan dan tidak memiliki meter kabel untuk menguji, apa metode lain bisa digunakan? Jawaban: Kita dapat menghubungkan perangkat yang berbeda untuk kabel untuk melihat apakah kabel mengaktifkan NIC pada perangkat. Selain itu, sebuah jack alternatif di daerah yang sama bisa digunakan




